| Application Series |
| Implementing an Elevator Access Control System Using FingerTec Terminals |
| Technical Support Team, FingerTec Worldwide |
Elevator access control plays a major role in of establishing a comprehensive access control system in high-rise multi-tenant facilities. There are many critical points of vulnerability for this kind of facilities with regards to elevator security and access. Control on elevator lobbies and elevators themselves are recommended to protect the inhabitants of the building. There are added benefits to securing access to elevators, such as effectively reducing the building’s risk of costly theft and damage to the structure. Implementing elevator access control measures is also a method to limit undesirable transient traffic. By using an elevator access control system, you can separate the general public and unauthorized users, from authorized users. |
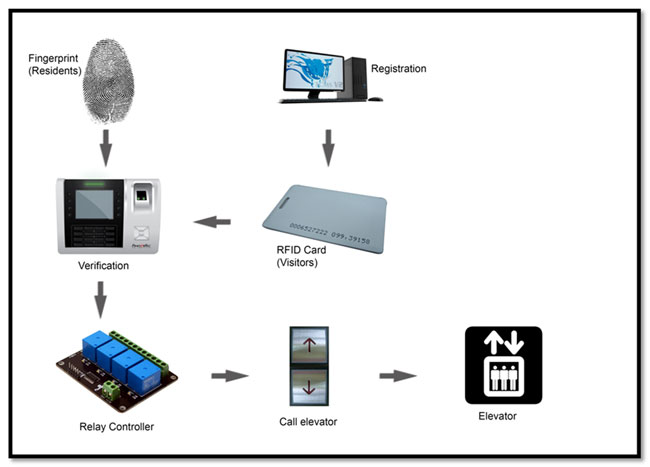 |
| Should biometrics system be preferred in the implementation of elevator access control system, then FingerTec Q2i is highly recommended to work as a capturing station to verify users’ identities. With biometrics technology implemented, you do not need to worry about leaving your access cards at home or face the high risks of your cards falling into the wrong hands. When the user verifies his/her fingerprint at the FingerTec Q2i terminal, the terminal will identify the user’s identity and will send a signal to the relay, allowing the elevator’s up and down buttons to function and be selected by users. For users who fail to verify their identity at the terminal, the elevator’s up and down buttons will not be accessible for them, thus preventing the users from using the elevator. For visitors, all they need to do is register at the security outpost and be given an access card for temporary access to the elevator. |
| The diagram below illustrates the installation of the elevator access control system using FingerTec Q2i: |
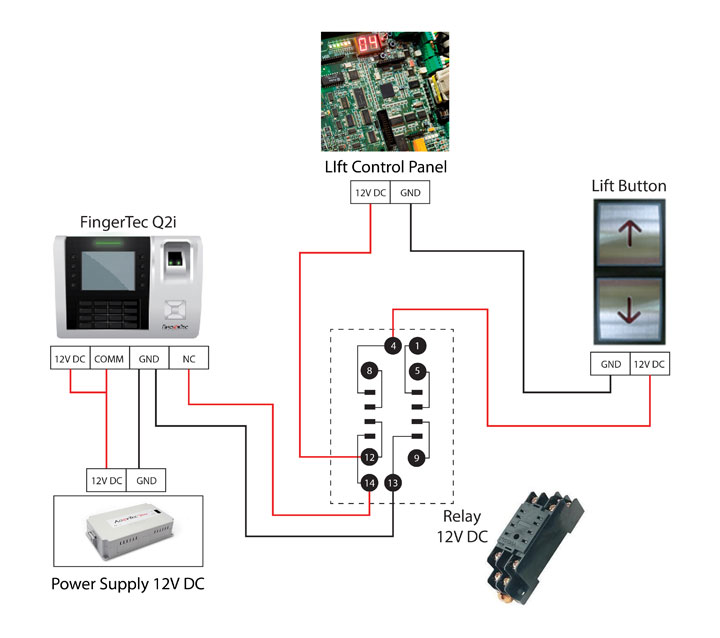 |
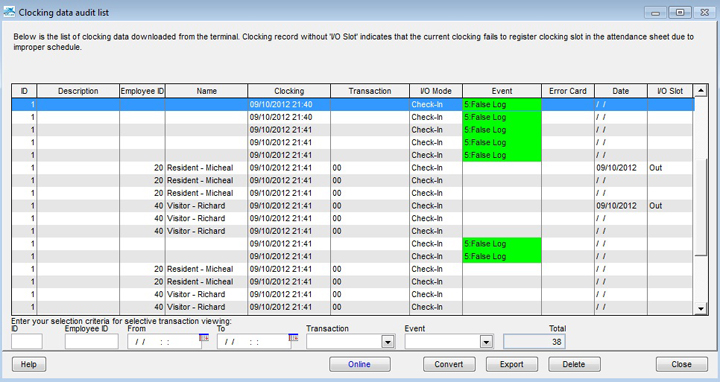
| With every unit of FingerTec Q2i, the time management application TCMS V2 is readily available in the package. TCMS V2 software controls as well as monitors the users’ access record around the clock. If there are any unauthorized users trying to access the elevator, the transaction record will be displayed as “False Log”. This "False log" indicates that the terminal has rejected the user’s verification. With the precise transaction data available, the security personnel can proceed to check the elevator’s CCTV for further action. The security personal can also opt to use the real-time monitoring function to single out any suspicious movements. |
 |
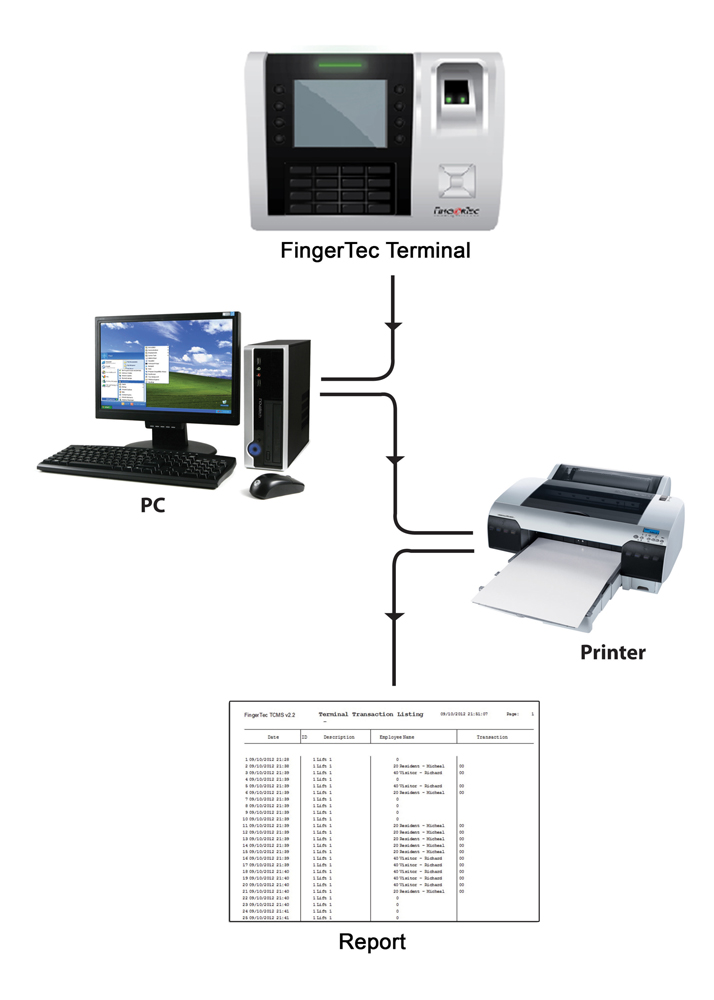 |
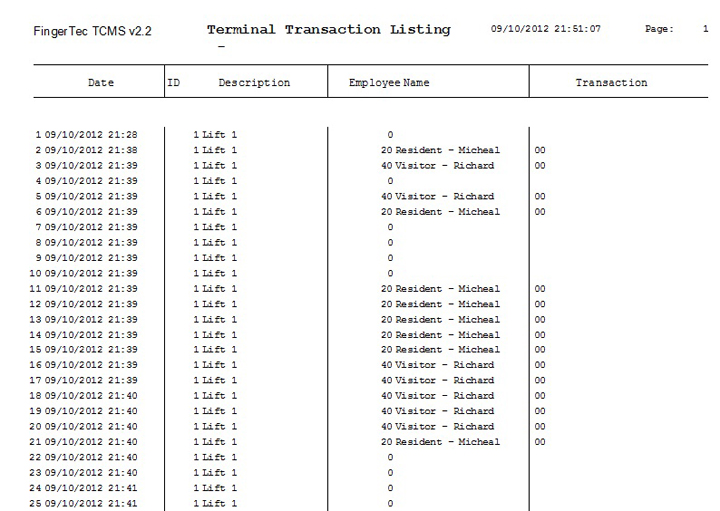
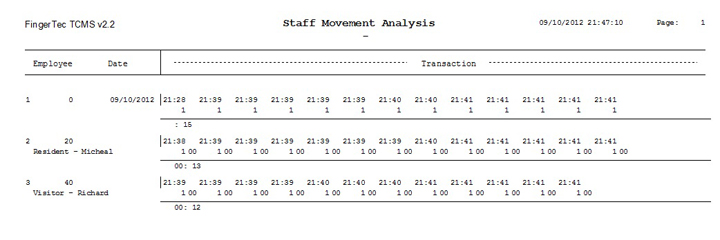
| By implementing this system, you will have an option to print out the transaction data for security reporting purposes. Below are samples of few reports that may come in handy. |
Terminal Transaction Listing Report |
 |
Staff Movement Analysis Report |
 |
| Tweet |
Copyright © 2012 FingerTec Worldwide Sdn. Bhd. All rights reserved.